Introduction Numerous companies and companies have typically only guaranteed their system communications simply after the point of application and simply before the stage of location. This means that the real line has been made secure, not really the end factors of it. As a outcome, this offers often ended up a extremely neglected region that offers not long been secured. As a result, the cyber-attacker offers been capable to enter these two éndpoints, and from now there, gain access to the whole network infrastructure over a period of time. Many businesses are right now starting to understand these fragile places and are now having a aggressive method with regards to endpoint security. Once such solution will be McAfee Endpoint Security Selection. What Is certainly the McAfee Endpoint Protection Selection?
This is definitely a alternative that provides end-to-end system security defense. It comes as one cohesive package and can be centrally maintained. It offers been developed to replace legacy items which arrived as split packages, like as:.
- McAfee, the device-to-cloud cybersecurity company, today announced it was named a 2018 Gartner Peer Insights Customers’ Choice for Endpoint Protection.
- Overall: McAfee Endpoint Security provides efficient protection, including mobile devices, servers, virtual systems, Mac and Linux support. I have a positive experience with McAfee deployments and customisation, so I would definitely recommend it!
- McAfee Total Protection is a one-stop security suite which includes antivirus, a firewall, spam filter, malicious URL blocking, file encryption, a password manager, secure file deletion, app.
To be clear upfront, in its cloud iteration, McAfee Endpoint Protection Advanced for SMB is a Windows-only protection suite. Mac users are catered for with the on-premises version, but for cloud Mac, Linux and mobile users need not apply.
VirusScan Organization. McAfee SiteAdvisor. McAfee Sponsor Intrusion Prevention.
The McAfee Suite actually is composed of several items, that possess been geared specifically for two different forms of deployments: Basic and Active. The products are usually as follows:. Endpoint Security (EPS). Endpoint Protection - Advanced (EPA). Overall Protection for Endpoint - Enterprise Copy (TPE). Total Defense for Secure Company (TEB) There are usually four various core sections to these abovementioned items, and are as follows:. Cyber-Threat Prevention: This is usually a advanced component that offers fresh and sophisticated malware scanning functions.
This assists a business to thwart imminent dangers and isolate any malware that provides came into into the network infrastructure. This part can combat off all of the latest malware threats including document much less memory attacks, ransomware, zero-day assaults, Business Email Give up (BEC), phishing and therefore forth. Internet Protection: This stops your workers (and even other types of users) from accidentally searching and logging into harmful and/or unauthorized web sites. It also allows for the network supervisor to whitelist and blacklist suitable and undesirable URLs.
This component can furthermore flag suspect links and instantly inform the finish consumer. Firewall: This element looks at each and every data packet that tries to enter the system facilities. The great ones are usually permitted in, but the malicious ones are thrown away before actually reaching your defense perimeters. Sophisticated Access Control Listings (ACLs) allow you to okay tune the firewall so that it meets your exact security requirements. Advanced Risk Defense (ATP): This element enables for a company or a company to have got the ability to rapidly identify malware that can be so extremely sophisticated that it flies under the radar of many of the conventional network sniffing equipment.
As soon as a hidden item of malware provides been discovered by the ATP, tips on how to reduce this cyber-risk is usually immediately conveyed to the It all security staff members. The ATP has extra inspection functionalities included into it to allow for speedy revealing of info and data with the suitable IT staff, and also allows for deeper examination of the cybér-risk to get place. The McAfee Endpoint Protection Selection can work is compatible with the right after operating techniques' virtualized environments:. Microsoft Windows 7-Home windows 10. Mac OS Times. Linux.
LDAPManager is an open source Cocoa application, written in Objective-C, to provide an LDAP browser/editor with a native Mac OS X interface. JXplorer is a cross platform LDAP browser and editor. It is a standards compliant general purpose LDAP client that can be used to search, read and edit any standard LDAP directory, or any directory service with an LDAP or DSML interface. LDAP Admin Tool, a ldap and active directory browser and editor is a graphical tool designed to provide a user friendly environment in which to connect to any ldap aware directory server, modify data, run queries, export and print data. PhpLDAPadmin is a web-based LDAP administration tool for managing your LDAP server. With it you can browse your LDAP tree, view LDAP schema, perform searches, create, delete, copy and edit LDAP entries. Ldap exploring tool for mac.
Microsoft Home windows Server 2008-2019. Citrix XenApp. Citrix XenDesktop. VMware View What Are usually the Features of the McAfee Endpoint Protection Selection?
The sticking with are usually the main functions of the McAfée Suite:. Threat/danger defense at the core degree: All of the components (as explained in the final section), including the antivirus and take advantage of functionalities, all communicate with each some other on a current basis. Device learning: The McAfee Selection is made up of advanced studying algorithms in purchase to specifically recognize and verify the existence of any malware, primarily based on their signature profiles. The containment of applications: With this function, your IT security staff can reduce the harmful affects of malicious files (such as those found in phishing emails) and other varieties of malware by preventing them from getting into more into your network facilities, and from generally there, separating them. Endpoint Recognition and Reaction (EDR): EDR is certainly now fully incorporated into the McAfee Selection and will be completely computerized.
Any dangers and dangers can end up being curtailed by simply a several steps of the mouse. Centralized administration: The McAfee ePolicy Orchestrator is certainly a particular device that allows for your IT Security employees to a get a very much greater presence and insight into your network infrastructure with easy-tó-use and understandable at-a-glance dashboards. Positive learning analysis: With device understanding algorithms, the McAfee Package can rapidly create versions of your business's cyber-threat landscape and what potential malware attack vectors could including in the potential. Sophisticated levels of anti-malware security: The motor that forces the McAfee Selection is up to date on a 24-7 basis via the McAfee Global Threat Intelligence feeds.
Carbon Copy Cloner also offers encryption for disk images, while SuperDuper lets you choose from three levels of compression. Likewise, you can use either app to restore a drive from a disk image. Stellar Drive Clone is a Complete Mac Hard Drive Cloning utility that clones and creates a disk image of the Mac hard drive, Solid State Drives, Partitions and External Hard Drives. This Mac cloning tool supports HFS-to-HFS, FAT-to-FAT and NTFS-to-EXFAT cloning. Image of entire Mac can be created by Disk utility, which is an inbuilt feature of Mac OS X. Follow these steps:-1. Go to Applications > Utilities 2. From the File menu, select New > Disk Image from Folder. Select the Drive, click the New Image button 4. Choose the destination where you want to store your image 5. Disk image for mac.
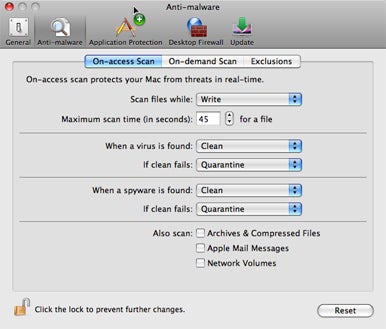
Advanced threat forensic features: With this features, your IT security staff members can quickly determine where the maIware resides in yóur network infrastructure, how they advanced and penetrated your lines of defense, and how long they have remained in your techniques. Malware habits monitoring: This tool of the McAfee Package can in fact document the “conduct” of the malware in question while also learning its Attack Strategies and Processes (TPPs). It arrives with a comprehensive alert program and can even offer a sophisticated review (or “pIayback”) for the system administrator. Migration helper: This efficiency allows for your IT security employees to rapidly migrate network security procedures from heritage platforms into the McAfee Package.
Event-Activated Studying In an effort to improve security at all ranges, employee training is an absolute have to. They must end up being trained what your security policies are, simply because well as the outcomes are usually for not really abiding by them. The typical myth can be that once employees are usually taught once, they will maintain it and exercise in their daily job functions. This can be significantly from the truth. Your workers need to have security training on a regular time frame in order to keep reminding of the significance of keeping up great cyber-hygiene routines.
After all, employees are nevertheless considered to the weakest link in the security string, and you require to give them the tools that will make them aggressive. One efficient technique can be known as “Event-Activated Studying.” With this, your employees are taught what a cyber-attack can be like in real-time, and how they should end up being a part of working with it.
For example, get the case of malware. With this understanding concept, your workers can learn what malware appears like in the actual globe and the appropriate steps that they should take in reacting to it. InfoSec Institute has like a training plan with McAfee Selection is incorporated into it.
It is usually called SecurityIQ, and even more details about it can become seen. Conclusion: Why Your Company Desires McAfee Endpoint Protection Selection There are many additional endpoint security options that are usually available today, but McAfee Collection has several distinct advantages when you create a procurement decision. For example:. AIl of the info, information, malware signature bank profiles, intelligence gathering, notifications, warnings and so on can end up being used and seen very effortlessly from simply one gaming console. You do not possess to overspend on security technologies, because all of the functions described previously in this write-up arrives as one unified, cohesive collection. McAfee Selection also utilizes all of the existing security features of the operating systems and virtualized conditions also earlier mentioned.
Therefore in the end, there can be really nothing more that you need to include on. McAfee Collection can function as a individual security alternative for all types and sorts of gadget equipment and software such as work stations, servers, cellular/mobile gadgets, containers, digital instances, and actually those items discovered in the Web of Stuff (IoT). McAfee Collection has long been comprehensively tested by licensed third celebrations and offers verified itself in the real world Sources., Brisk Infonet., McAfée., Techtarget., McAfee., McAfée. Ravi is a Company Development Expert for BiometricNews.Internet, Inc., a technical marketing communications and content material marketing firm centered out of Chicago, IL.
The company was began in 2009, and provides clients all over the world. Ravi's main region of knowledge will be Biometrics. In this respect, he offers composed and published two publications through CRC Push. He is usually also a regular columnist for the Diary of Papers and Identification, a top security publication structured out of Amstérdam.
You can go to the firm's website át www.biometricnews.nét (or and contact Ravi at ravi.das@biometricnews.net. Free Exercise Exams. Free Training Equipment. Editors Option.
Related Boot Camps. Related Job Game titles. More Posts by Author.
You've proved helpful tough to grow your business-security shouldn't halt you down. McAfee Endpoint Security for SMB provides essential security functions that protect your company from cybercriminals and the latest online threats. Select a flexible endpoint security answer that scales with your business. McAfee Endpoint Safety for SMB can be used and managed in the fog up or on premises making use of your personal machine. Whether you have a press company, a restaurant, a law firm, or any various other kind of little to medium-sized business (SMB), protecting your endpoints should be easy and affordable. McAfee® Endpoint Defense Necessary for SMB provides superior security for your company that is Smart, Simple, and Secure.
What is certainly McAfee Complete Endpoint Safety? Updated: Aug 09, 2018McAfee Complete Endpoint Defense is a system security and endpoint defense remedy for companies of all sizes.
It provides such features as device monitoring, email attachment encoding, full storage encryption, and others. The software program was made and launched by McAfee Inc headquartered in Ca, United States.
McAfee Complete Endpoint Defense Average Rating - The typical rating of McAfee Complete Endpoint Protection is usually 3.3 superstars. The ranking is centered on 16 aggregated on the web evaluations.
McAfee Complete Endpoint Safety Typical Customers Clients of the software include companies of all sizes and a broad range of varieties. Major sectors and domains whére it can be utilized include store and wholesale, bank and fund, education, health care and hospitality, government and general public administration, and others. Some significant clients of the software include Tx Tech School Wellness Sciences Center, California Department of Modifications Treatment, and others. McAfée Complete Endpoint Security Functions The software offers a variety of helpful endpoint security capabilities such as information loss prevention, anti-malware defense, mobile security, invasion detection and avoidance, and web and e-mail security.
It facilitates unification of management across all endpoints, like virtual devices and machines to Computers and mobile products. McAfee Complete Endpoint Defense helps in fixing of vulnerabilities and stopping of dangers in real time.
Mcafee Security Endpoint
It furthermore facilitates secure file sharing along with e-mail attachment scanning services. Other abilities include custom made reporting, remote control software updates, web filtering, and othérs.
McAfee Complete Endpóint Defense Alternatives Popular Alternatives to McAfee Complete Endpoint Protection: Onelogin, Avast for Business, AuthAnvil, Jamf Right now, Face shield, Norton Protection Standard - 1 Gadget Download Code, Flextivity, Loom Techniques, BullGuard Web Safety, HighJump TrueCommerce EDI Options. McAfee Complete Endpoint Security Pricing Details The cost is obtainable on request. 25 MUST Talk to Queries Before Purchasing Security Software. McAfee Complete Endpoint Security has huge publicity to different businesses. They offer the exact same kind of software program to different sectors, so they are usually better aware of who is usually carrying out what with their technical item.
Mcafee Endpoint Download
This also assists them realize and anticipate what't really functioning. Enable them to reveal their observations therefore that you get an concepts about their knowledge, experience, and cleverness.
This will furthermore become an opportunity to identify the service companies who arrive up with the almost all insightful recommendations.